8 Top Cybersecurity Threats To Businesses [& how to protect your business]
8 Top Cybersecurity Threats To Businesses [& how to protect your business]
When the Covid19 pandemic hit, more than people’s bodies became endangered by malicious viruses.
As people began working from home to avoid Covid19, they put themselves at risk for another virus - computer viruses.
The switch to remote work has caused a huge increase in cybercrime over the past year, which leaves many business owners wondering: Is my business safe from cyberattacks?
We get it that you may be on edge. After all, 2,200 cyberattacks happen per day. That’s 1 cyber attack every 39 seconds. Cybercrime is a real threat!
Thankfully, Boomtech’s IT team is here to help!
Along with our business cybersecurity solutions, we put together a list of common cybersecurity threats you should be aware of and some tips on how you can protect your business. We want to help you protect your business and avoid being a cyber-attack statistic.
Ready to learn how you can keep your business safe?
Let’s find out!
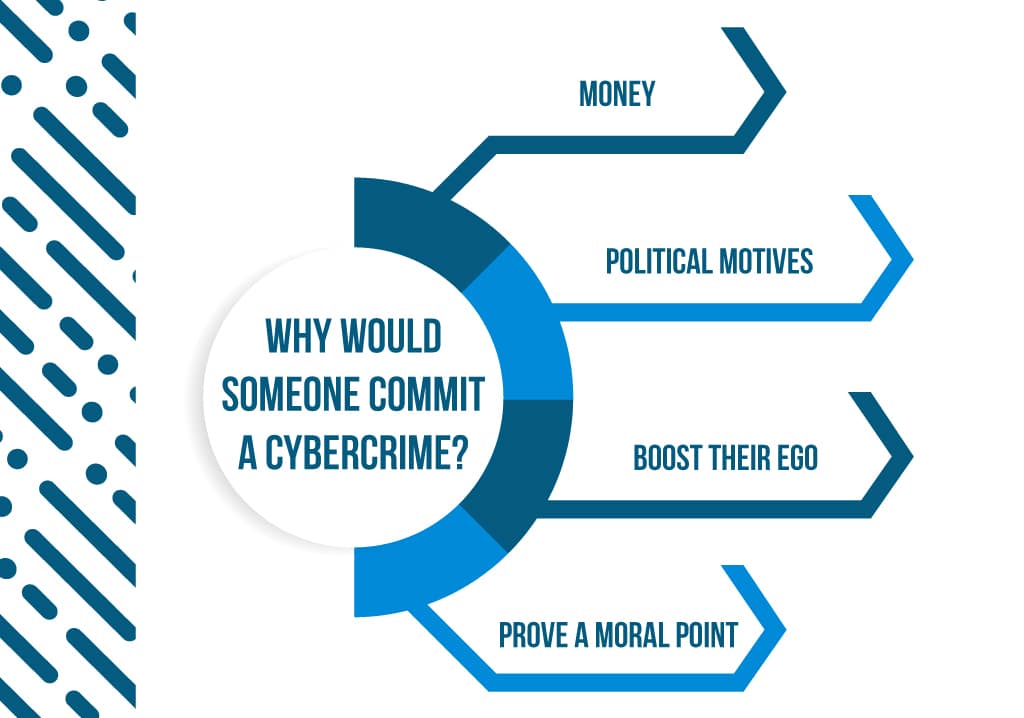
Why Would Someone Commit A Cybercrime?
Before we start, let’s back up for a moment. What are the reasons someone might commit a cybercrime?
As you might guess, there are a variety of reasons:
A lot of cybercriminals simply want money. These criminals might steal personal information and sell it, use incriminating information for blackmail, or hold files for ransom - anything to make some cash.
Other hackers have political motives.
They might want to access incriminating emails, sensitive military information, or government records. Or they might want to mess with the workings of military equipment or government websites. These people might be from an opposing political party, another nation, or a terrorist group.
Finally, some hackers want to boost their ego or make a moral point. Hacking a tough site shows it can be done, and can add feathers to your cap in the hacker community. And some people even hack to make ethical or moral points, such as in the Ashley Madison drama of 2015.
Who Is At Risk For Cybercrime?
Who do cybercriminals tend to target?
The answer to this question is somewhat surprising.
You might think hackers would target large businesses because it seems they could make the most money that way.
Lots of small business owners think “Not me! Things like cyberattacks don’t happen to me.” Or “Why would someone be that interested in my smaller business?”
But actually, hackers tend to target small to medium businesses because smaller businesses don’t often have the budget for great cybersecurity measures. Hackers know this and take advantage of it.
So when you think “Not me” you actually are the one at risk!
No business is completely safe from cyberattacks, especially ones that close their eyes to facts.
The good news is that realizing you are not immune to disasters like cyberattacks is the first step toward preventing them.

8 Top Cybersecurity Threats To Watch For
How exactly might a cybercriminal attack your system?
Let’s find out!
Here are some common types of cyberattacks. Be on the lookout for these threats so you can stay safe!
Malware
Malware is a blanket term for different types of malicious software. It is any type of software hackers use to infect systems and interfere with their normal functioning.
Malware includes viruses, trojans, spyware, ransomware, and other destructive types of software.
Most types of malware infiltrate a system when the user clicks on or downloads something phony. A pop-up might say something provocative like “Claim your prize!” or “Your system is compromised. Click here to run a scan.”
When the user clicks the pop-up, their computer is infected.
I mean, one wrong move and your computer is infected? Not cool!
After they are in the system, different types of malware act in different ways, depending on what the hacker wants to do. They might spy on a user and collect data about them, lock data up till a ransom is paid, or spread more malware.
The options are sinister and endless!
Now let’s go on to discuss some specific types of malware and other cyber threats.
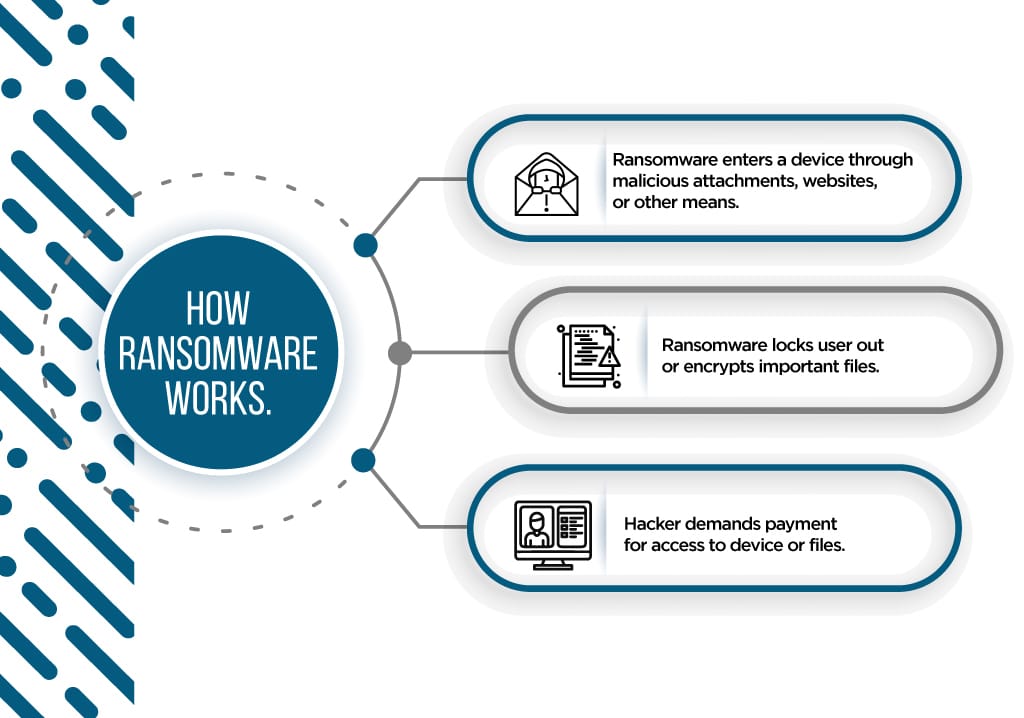
Ransomware
Ransomware is a type of malware. Here is how it works:
The ransomware enters a computer, maybe through an email with malicious attachments or a sketchy website.
After that, the ransomware can lock the victim out of their computer or encrypt important files. Then the hacker demands a ransom payment (often in cryptocurrency) before the victim can re-access their files.
It is never recommended to pay the ransom if your computer is infected with ransomware, even if it is the cheapest and easiest course of action. Paying the ransom doesn’t guarantee you’ll get your data back, and it encourages more ransomware attacks.
Contact an expert immediately if you ever encounter ransomware. They can help you determine the best plan of action.
Of course, it’s better to prevent ransomware in the first place. Here are some good ways to avoid ransomware:
- Keep your technology up to date
- Avoid clicking suspicious links or pop-ups
- Back up your data regularly
- Use only known download sources
Trojans
Named after Homer’s famous Trojan horse, a Trojan is a type of malware disguised as legitimate software. Users install or download Trojans thinking they are useful applications, but in reality, they are imposters.
After it infects a computer, a Trojan could do several things. A “Backdoor Trojan” lets attackers access and control your computer. A “Downloader Trojan” downloads and installs more malware. An “SMS Trojan” infects your smartphone and intercepts text messages.
And there are a lot more types of Trojans!
If you want to avoid Trojans, simply be careful what you click. The user must click, download, or install Trojans for them to work, so if you are alert, you may be able to detect and avoid them before they infect your computer.

You can also get anti-virus software that is pretty good at catching Trojans.
So be careful what sites you visit, what pop-ups you click on, and what you download. Don’t ever open a link in an email unless you are sure you trust the sender.
It pays to stay alert and careful!
Phishing
“Phishing” is a wordplay on “fishing,” (and is pronounced the same way) and it’s the practice of sending shady emails that try to get users to reveal sensitive information. Essentially it’s fishing for information.
For example, a hacker might send an email that looks like it’s from Microsoft 365 that requests a login. If the user falls for it and “logs in,” the hacker now has their Microsoft 365 login credentials.
Not cool!
Spear phishing is a common type of phishing attack that targets a specific individual instead of a wide group of people. This way, the attacker can customize their attack for a certain person.
People who put lots of personal information on social media are often targets for spear-phishing attacks because if hackers know about your hobbies, family, and interests, they know how to craft emails that will capture your attention.
Like with Trojans, prevention for phishing attacks is fairly simple:
Be careful what you click and what information you give out!

Do not click on any link or attachment in an email that looks suspicious. Never share any personal information unless you completely trust the sender. If in doubt, give the sender a call and make sure everything is above board.
You can also be on the watch for phony URLs. If you aren’t sure about a site, search for the real site and compare URLs. If the URLs are different, one of the sites is a scam.
Smishing
Emails aren’t the only avenue hackers use to get information.
Smishing (or SMS-based phishing) is a type of phishing where criminals send phony text messages that try to get users to reveal information or click bad links.
The text messages often use social-engineering techniques and urgency to get users to take immediate action.
For example, during the holidays, you might get a message that looks like it’s from Amazon telling you to verify your billing information, or you won’t get your package in time for Christmas.
Or, during tax season, you may get a text message disguised to look like it’s from the IRS. These messages often threaten to freeze your tax return if you don’t open the link to verify some piece of personal information.
However, the links in these messages take you to a fake website, and the personal information you enter is used for fraud and theft.
Don’t interact in any way with messages that look shady! Do not click links and do not reply or call an unknown number, even if the message says “text ‘stop’ to opt-out.”

If the message is spoofing a known business, look up the business’s phone number and call them directly to see if the message is legit, but never call the unknown number.
And never, ever enter your password unless you are logging into an actual site. For example, never log in to your Amazon account unless you searched for Amazon in your search bar.
PDF scams
PDF scams are a common type of phishing scam. A scammer will send an email with an attachment that asks you to do something like:
- “Click here and enter your email credentials to access your file”
- “Verify your account details”
- “Confirm your payment information”
The goal is to get you to click on the PDF, and scammers have tons of tricks for getting you to do this.
Needless to say, never click on a PDF and never enter your credentials unless you are sure an email is legit!
Some of these scams are very advanced and might trick anyone. The best way to avoid them is to educate yourself on the techniques scammers use to trick people. That way, you can know what to avoid.
If you have questions, always make sure to contact your tech support before taking action.

Credential Stuffing
Credential stuffing works like this:
A cybercriminal obtains a list of credentials from a data breach or buys stolen credentials on the darknet.
The criminal then takes that list of credentials and attempts to use them to log in to other services, hoping that someone has used the same username and password for multiple services.
For example, a criminal could obtain a list of usernames and passwords from a retail store and try using them to log in at a bank, hoping that some of the store’s customers also have accounts at the bank and used the same username and password for both accounts.
Credential stuffing has a very low success rate, statistically speaking. Only about one in a thousand attempts results in a cracked account. However, it’s not hard for a criminal to buy millions of credentials on the darknet and use bots to stuff these credentials on different sites. A set of a million credentials might yield a thousand cracked accounts. Bad news, right?
And the good news?
It’s easy for users to prevent themselves from being hacked this way.
If you never used the same set of credentials for two services, credential stuffing would be impossible. So if you always use unique usernames and passwords for different services and sites, you are not at risk for this threat.
If you feel like you are going to have trouble remembering all those unique passwords (I mean, some of us can’t even remember our anniversaries!) you could get a password manager like LastPass. A password managing app of this kind helps you generate, save, and secure passwords for all your logins.
Accidental sharing
You might have watertight cybersecurity measures in your business. But they can’t completely account for one thing: human error.
Mobile devices get lost, employees accidentally send emails to wrong addresses, information gets forwarded to personal email accounts...mistakes happen.

In recent years, the risk of accidental sharing has grown due to several things:
One factor is the growing number of ways employees can share data - email, messaging apps, collaboration tools like Slack and Dropbox, and so many more. The other factor is the cultural need to share everything immediately. These two factors combine to create a hotbed for accidental sharing.
In fact, 83 percent of security professionals believe that employee error has put their business or customer data at risk.
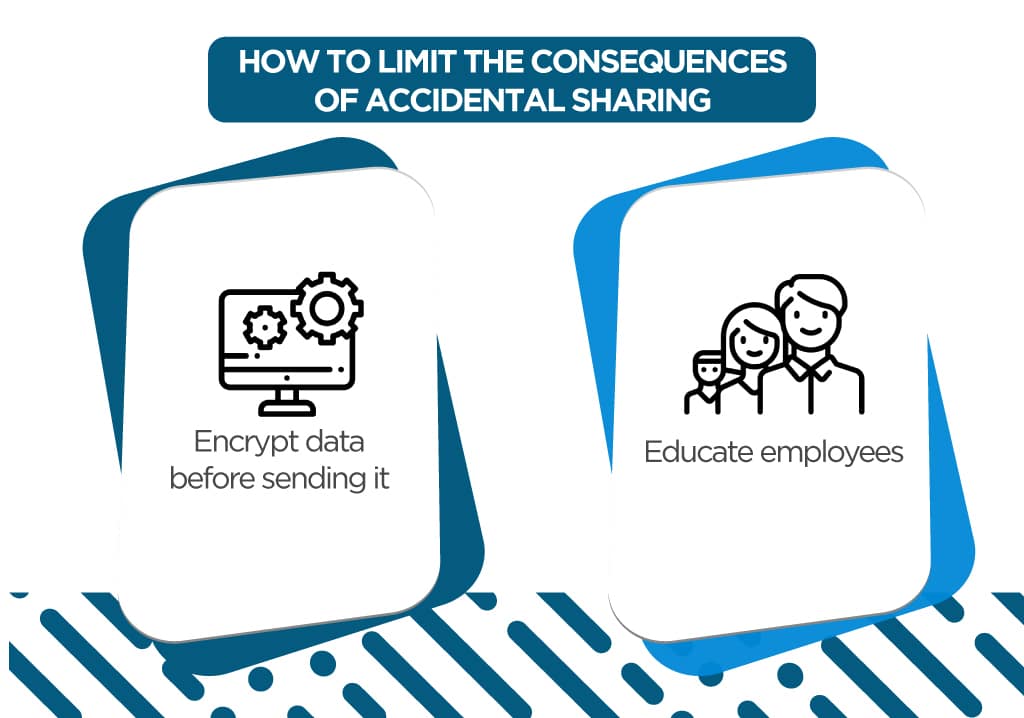
There are two main ways businesses can prevent or limit the consequences of accidental sharing:
One is to encrypt data before sending it. Encryption is a great way to protect data that might fall into the wrong hands. There are lots of different encryption tools for various purposes.
The other way is to educate employees. Write down your company’s rules for sharing sensitive information and make sure your employees know the rules. Be sure your employees know what is classified as sensitive information and how to share it properly.
We will never completely eliminate human error, but precautions such as these go a long way towards keeping your data safe.
Conclusion
Will you ever be 100% safe from cyber-attacks and data breaches?
Unfortunately, no.
As long as computer data exists, clever cybercriminals will come up with new ways to steal it for their own purposes.
However, the first step toward prevention is simple:
Be aware.
Educating yourself about cybercrime helps you take the right steps toward keeping yourself safe.
Prevention is better than cure, so don’t wait!
If you ever need help with your cybersecurity in the South Florida or Miami regions, contact us here at Boomtech!
Our team of IT experts can help you implement the right safety measures to protect yourself against threats like the ones we learned about in this article.
We provide various IT services, including managed IT, cybersecurity, cloud strategies, and disaster recovery.
We make it easy to work with us!
- Schedule a free consultation
- Schedule a second meeting
- Get a proposal
- Onboard!
Specializing in law firms, CPA firms, financial firms, and the wholesale industry, we promise to do our best for your business.
Give us a call today! We look forward to hearing from you!