6 Cybersecurity Measures Every Distribution Company Must Take [& 8 reasons it matters]
6 Cybersecurity Measures Every Distribution Company Must Take [& 8 reasons it matters]
When you think of wholesale distribution, scenes of loud machines and huge warehouses likely come to mind.
And if you were to consider how you would secure a wholesale business, you’d probably consider things like securing the perimeter of the building, screening everyone who enters, and monitoring the facility with cameras.
But the fact of that matter is that wholesale distribution and its related technologies are developing at an extremely rapid pace - and along with these new technologies come brand new IT and cybersecurity concerns.
In fact, supply chain cyberattacks are becoming frequent occurrences.
To assume that your distribution business is impervious to cyberattacks is setting you up for almost inevitable failure.
But what can you do to avoid these devastating attacks and run your business smoothly?
Rest assured - you aren’t powerless against cyberattacks. At BoomTech, we’ve been helping businesses with IT and cybersecurity concerns for years - and today, we want to put our years of experience to work so you can secure your company.
Ready to go? Let’s get started!
Table of Contents
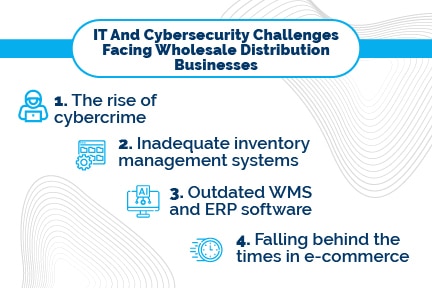
IT And Cybersecurity Challenges Facing Wholesale Distribution
Running any kind of business requires intelligence, hard work, and perseverance. But the rapidly changing landscape in the distribution world has caused a few particular problems.
Let’s take a moment to identify a few of these problems.
The Rise Of Cybercrime
In 2020, manufacturing was the second most targeted industry by cybercriminals. And while manufacturing is not the same thing as distribution, this statistic reveals an important truth:
Cybercriminals are beginning to recognize how interrupting the supply chain is a sure way to get what they want.
The most recent example is the Colonial Pipeline that hackers targeted. The pipeline is a major fuel supplier for the east coast, and when hackers were successful in their attack, nearly half of the U.S. East Coast’s fuel disappeared.
The result?
The hackers got precisely what they wanted - millions of dollars.
We know how easy it is to think that hackers will not target your business. But we’re pleading with you to see past that deception.
Cybercrime becomes more prevalent every year - and without proper security measures, it is truly only a matter of time until your business becomes the next victim.
On the other hand, partnering with an experienced IT business can save you from the scary reality of cybercrime.
Inventory Management
If you’re thinking of becoming a distributor and aren’t sure what “inventory management” means, it’s the practice of keeping track of all the goods coming in and going out of your storage facility.
Inventory management issues are nothing new in the distribution industry, and a complete solution is yet to be developed for this incredibly complex problem.
Traditionally, inventory management has been tackled in one of two ways:
- Products were manually counted (which is exhausting and time-consuming!)
- RFID tags were utilized (which are incredibly expensive)

Thankfully, inventory management software like Oracle NetSuite and Iptor are beginning to provide cost-effective and efficient solutions to managing stock.
However, the addition of powerful pieces of software also creates more spaces for processes to break down on the technical side of your business.
And when your entire inventory management system goes down, you are in a whole world of hurt! It’s essential to have a reliable IT partner that can troubleshoot any issues that come up and address them immediately!
Inadequate WMS and ERP Systems
In today’s world, we want things quickly. In fact, most of us have likely experienced not buying something on Amazon because it doesn’t have 2-day shipping!
That means distributors have to move a lot of material in a short amount of time.
If your systems and processes aren’t highly optimized and organized, there’s a good chance you’ll fall behind and eventually out of business.
This is where Warehouse Management Systems (WMS) and Enterprise Resource Planning (ERP) software come in. Both are the backbone to running a successful distribution or wholesale business.

A Warehouse Management System (WMS) is mainly used to manage the movement and storage of inventory within a warehouse. It tracks the movement of each inventory item, such as the item being received, put away, picked, packed, and shipped.
Beyond that, a good WMS offers benefits like:
- The ability to set up stocking and non-stocking locations to show the true count of inventory while at the same time separating product available and product already allocated to an existing order
- The ability to set up stocking location priorities and ratings for more efficient picking
- Precise movement tracking of product – from the shelf, to cart, to specific stations.
- Cross-docking features which provide employees the ability to receive and ship products without putting it away.
ERP software is similar but has a slightly larger role.
The primary purpose of ERP software is to facilitate the flow of information between all functional areas of a business.
That means it automates business practices across all departments, including accounting, order entry and processing, purchasing, inventory management, warehouse management, eCommerce integration, and customer relationship management.
Both ERP and WMS are a part of supply chain management and aim to help businesses manage their resources in the most economical way possible.
When they do the job, you are in great shape!
Unfortunately, many distribution and wholesale businesses have been slow to upgrade to high-powered WMS and ERP software that can keep up with the demand of their companies.
Rise Of Business To Consumer E-commerce
Small businesses have been sneaking up on wholesale distributors for years. They’ve been building beautiful, optimized websites and offering excellent customer service.
Now distributors are rushing to create a quality online presence as well.
The problem is that many distributors - especially those who’ve been in the industry for years, don’t know how the world of online sales works.

In most cases, their website existed to serve their existing customers by giving them the option to order stock online instead of over the phone.
So, the shift to a competitive online presence is vital for distributors.
But when an entire industry shifts over to an entirely new platform, there will be major problems - particularly at the beginning.
A huge problem is simply having the information and knowledge to keep an online presence maintained and optimized.
If that’s enough, entering the online world creates another portal for cybercriminals to attack a company.
Whichever issue you face, investing in a trusted IT company is definitely worth your time and money!
The Importance Of IT Management And Cybersecurity In Wholesale Distribution
Ok, let’s get practical.
You know that protecting your distribution business is important - that much is logical.
But what are the consequences of poor IT and inadequate security measures?
Extended Service Unavailability
When technology breaks down, failure to resolve the problem as soon as possible leads to compounding issues that affect the staff involved and customers and other employees who are dependent on the output of that staff.
Extend the IT problem to more than one person in the organization, and you will have exponentially increased the number of inconvenienced employees or customers and the gravity of the issue.
Poor Customer Service
The only thing worse than dealing with an irate customer is losing that customer altogether.
Unfortunately, poor IT management can lead to both issues.
In today’s world, any tech-related incident requiring IT support that would disrupt customer servicing—a computer breakdown, software crashes, or slow internet connection, could leave a lasting impression on them.

And the worst part?
Dissatisfied and upset customers can tell others about their bad experiences in a hurry. Just a couple of tweets or Facebook posts and the floodgates can open for a social media nightmare.
Poor IT Support Can Cost You Money
Did you know that four in ten businesses claim to have lost sales due to a lack of IT support?
That means that IT support can directly influence the financial stability of your wholesale business.
Whether it’s due to loss of sales and business opportunities, lost productivity, equipment breakdown from poor maintenance, computer malware, data breaches, or any other technology issue, ineffective IT support could significantly impact a company’s bottom line.
Loss Of Productivity
One of the main effects of a cyberattack is lost productivity.
This starts with staff time directly consumed by the incident – following an attack, routine IT work is likely to grind to a halt.
Even after normal operations resume, you will still need your IT staff to perform cleanup, determine the root cause, fix vulnerabilities, and reinforce security, or assist external assets in this process.
Of course, if you don’t have a dedicated IT team, this becomes a whole new issue and will take even longer to resolve!
And as IT personnel deal with the technical side of things, there is a good chance other staff may be left without access to critical systems and processes.
Thankfully, that helpless, frustrating feeling can be avoided by hiring an IT professional that can protect your business.
Supply Chain Disruption
There’s an adage that says, “A chain is only as strong as its weakest link.”
In other words:
It doesn’t matter how strong a chain is - if it has one vulnerability, the whole chain is still vulnerable to breaking, and therefore not fulfilling its purpose.

The world of wholesale distribution is essential in supply chains for countless materials. You don’t want to be the weak link in the supply chain.
However, if your business isn’t properly secured, a cyberattack can make you the weak link in the blink of an eye.
Not only will your own business be hurt, but other businesses and likely hundreds of consumers are affected as well.
If you don’t want to be the weak link in a supply chain, make sure you have an IT team that can secure your distribution business.
Data Theft
Data theft is more prevalent now than ever before, impacting major corporations all around the world.
From basic information about inventory levels to personal details about individual customers, an assortment of data must be guarded and encrypted to make sure it does not get into the wrong hands.
And when a data breach does occur? You might say the results are disastrous. You’ll deal with things like:
- Regulatory fines
- Ransomware demands
- Investigation costs
- Covering victim’s costs
Shipment Theft
Another concern that comes with data theft is the potential it creates for product theft.
For example:
If criminals were to get their hands on the shipping details for an important set of packages, they would know the location where the products would arrive and when they would be arriving.
In essence, the leaked information would provide a map and guide that gave the thief everything he or she needed to know to gather the package and sell it without the company’s knowledge.
With cybersecurity in place, this information is only exchanged between authorized members of the supply chain and shipping process.
Damaged Reputation
Trust is the most crucial ingredient in any relationship - whether it be a spouse, friend, or customer.
Unfortunately, a cyberattack can destroy trust - especially if your customers were directly influenced or if their information was involved.
That’s why cyberattacks have long-term consequences - far beyond the immediate frustration of being less productive or paying a fine.

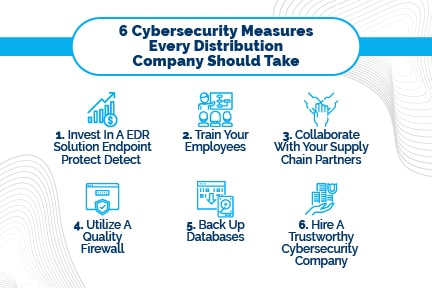
6 Cybersecurity Measures Every Distribution Company Should Take
The threat of a cyberattack on a distribution company is very real - and the consequences are tragic if not ruinous.
But we don’t say that to send you cowering into a corner, wringing your hands, and hoping you aren’t the next target.
We’re telling you this so the curtain can be pulled back. Now you’re aware of the threat - and the good news is that you aren’t helpless.
There are steps you can take to protect yourself from cybercrime!
Invest In A EDR Solution Endpoint Protect Detect
From Advanced Persistent Threats (APTs) to fileless malware, organizations today face a range of cyber threats that legacy security products simply miss.
Attackers have become highly adept at outmaneuvering signature-based protections like anti-virus software and Intrusion Detection Systems (IDS).
In particular, hackers like to focus on endpoints.
Endpoints – the laptops, smartphones, and other devices we use on a daily basis – are an easy target. They’re everywhere, prone to security vulnerabilities, and difficult to defend.
That’s why an Endpoint Detection and Response (EDR) Solution is so important.
Endpoint detection and response (EDR) is a category of solutions that can detect and respond to suspicious activity on an organization’s desktops, laptops, and mobile devices.

At BoomTech, our endpoint security monitors your IT environment, detecting malicious threats and quickly remediating attacks. You also get 24/7 support from our experienced security operations center (SOC).
The result is way more than anything you’d ever get from some kind of antivirus software.
We can keep up with things like multivariate ransomware attacks and the latest crypto-mining infiltrations.
And best of all? It’s backed by a one million ransomware warranty.
Train Your Employees
When you think about getting hacked, it’s easy to imagine someone in a hoody in a dark room, covertly tapping into your company systems.
However, it’s more common that the threat comes in the front door!
Social engineering attacks rely on human or social interaction, not just bots entering a computer through the internet.
And because humans are prone to error, social engineering is the biggest security risk today.
You can cut down on your risks significantly by training your employees in a few basic matters:
- Don’t open suspicious emails
- Don’t click on unknown URLs, links, and email attachments
- Prevent employees from downloading unauthorized software and apps
Collaborate With Your Supply Chain Partners
Many times cyber threats come from partners within your supply-chain network.
To increase efficiency in the distribution industry, you and those in your network must access shared online platforms. Therefore, you need to be cognizant of new vulnerabilities that may arise.
Even though you cannot control others’ security measures, you can choose to work with partners that conduct regular security audits or have external security certifications.
You could also devise a contract that requires your partners to adhere to basic cybersecurity measures.

Utilize A Quality Firewall
A firewall is a network security device that monitors incoming and outgoing network traffic and permits or blocks data packets based on a set of security rules.
Its purpose is to establish a barrier between your internal network and incoming traffic from external sources (such as the internet) to block malicious traffic like viruses and hackers.
But, before implementing firewalls, do your homework.
The effectiveness of conventional firewalls is limited to the extensiveness of their cybersecurity signature libraries. The latest generation of firewalls provides protection from the inside out and further segments valuable IT assets.
You’ll also need to ensure that all firewalls are correctly configured to block access to known malicious IP addresses.
Back-Up Databases
As a precaution, you should regularly back up important data, such as customer contacts and order information, in multiple locations.
Why?
If a hacker locks you out of the system or encrypts your files, all of your data will still be accessible on external hard drives.

While you’ll still have a mess on your hands, you won’t be in nearly as much trouble!
You’ll also want to make sure you backup and cloud applications you utilize like Microsoft 365 and Google apps.
While some of these cloud-based applications claim to perform backups for you, that isn’t entirely true.
For example:
Microsoft 365 offers basic protection to deal with some risks that could damage your data, but there are things it doesn’t protect you from, and there are side effects to some of its optional protection features.
Even if you feel you are well protected, the restore might be time intensive and quite a bit more work if you don’t have a third-party backup tool
Hire A Trustworthy Cybersecurity Company
Does all of this security language sound daunting?
If so, we get it.
Putting a digital security plan in place for your company is essential but very daunting - especially if technology isn’t your forte.
Hiring a professional IT company like BoomTech is a great place to start.
They should be able to help you with services like network security, web filtering, and a firewall.
3 Recent Cyber Attacks In The Wholesale Distribution Industry
Sometimes, nothing helps a concept make more sense than to hear about a real-life story.
Let’s take a look at several digital security breaches in the distribution industry.
Hackers Stole 220GB of Data in Toll Group Ransomware Attack
Toll Holdings Limited provides express freight transport by road, rail, and sea.
The company also provides integrated logistics and distribution systems, including specialized warehousing, port operations, and vehicle transport and distribution.
Unfortunately, this company was compromised with ransomware, and hackers stole massive amounts of data, in addition to locking systems with ransomware.
The company refused to pay any ransom, but according to a report on Data Breach Today, some of the stolen data was published on the dark web, including financial reports, invoices, and much more.
Bombardier Suffers Cyber Attack
In February 2021, Canadian plane maker Bombardier announced it had suffered a cybersecurity breach.
An initial investigation revealed that an unauthorized party accessed and extracted data by exploiting a vulnerability affecting a third-party file-transfer application, which was running on purpose-built servers isolated from the main Bombardier IT network.
The company acknowledged the attack after some of its data surfaced on the ransomware gang Clop's dark web portal.
Many security experts are speculating the attack is part of the Accellion "supply chain" breach.
In this specific breach, personal and other confidential information relating to employees, customers and suppliers were compromised.
Bombardier also admitted that designs for airplanes and plane parts are now available for free on the dark web.

ASCO Industries Furloughs 1,000 Employees Due To Cyber Attack
On June 7, 2019, a ransomware attack on Belgian aerospace supplier ASCO Industries forced the company to shut down production lines at four different factories across North America and Europe.
The attack was so damaging that the company furloughed nearly 1,000 employees temporarily and was out of operation for more than a month.
"Greater connectivity and digitalization are making manufacturing and supply chain operations more vulnerable to cyber-threats. Factories and logistics facilities can be caught in the crossfire of large-scale cyberattacks by criminals or state-sponsored groups, but they are also being targeted directly by a variety of actors," a report about the incident stated.
This incident shows just how crucial it is to have a layered approach to security that goes beyond stopping hackers from getting in or just cleaning up the mess after they’ve already done damage.
Conclusion
Let’s not beat around the bush - if you haven’t already, it’s time to start protecting your distribution business from a security breach.
We encourage you to take all the security measures you can on your own - but also acknowledge that the work of combating cybercrime requires professional expertise.
If you are looking for an IT provider or a partner to secure your business in Florida, or the #1 IT service provider in Boca Raton, then contact us.
We know security IT in and out, and beyond that, we offer services like business phone and communication solutions and business continuity solutions.
And the best part?
Working with us couldn’t be easier. All you have to do is:
- Schedule a free consultation. We’ll discuss your goals and see how we can help.
- Get a proposal. You’ll get to experience what it’s like to be our client.
- Onboarding. After the proposal is signed, our team takes care of the onboarding work, and you are set to go!
Contact us today. We look forward to hearing from you!


